In these scenarios, Nastran In-CAD's comprehensive set of post-processing tools can prove to be helpful. Since there are many post-processing tools available within Nastran In-CAD here will initially discuss Fringe Display plots.
The main benefit of using fringe results is that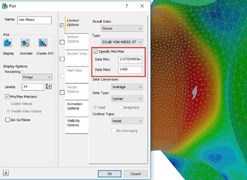 once we alter the maximum value of the legend bar any value higher than the new maximum will be displayed as grey. This can prove to be very useful as we can use this technique to isolate high stresses due to singularities and concentrate on the area of interest.
once we alter the maximum value of the legend bar any value higher than the new maximum will be displayed as grey. This can prove to be very useful as we can use this technique to isolate high stresses due to singularities and concentrate on the area of interest.
It is important to no te that altering the maximum value is not about fiddling (non-technical term) with results but is merely about presenting results which are meaningful. Once we have a minimal grey area we can use the probe tool available within Nastran In-CAD to display the maximum value. The benefit of using a fringe display and probes like this is to help locate the maximum value location with ease in the area of interest within the model.
te that altering the maximum value is not about fiddling (non-technical term) with results but is merely about presenting results which are meaningful. Once we have a minimal grey area we can use the probe tool available within Nastran In-CAD to display the maximum value. The benefit of using a fringe display and probes like this is to help locate the maximum value location with ease in the area of interest within the model.
I hope you find this tool helpful, and continue with the next blog in this series 'Exploring corner stress plots'



