Cracks in the System
Cybersecurity threats don’t always kick the door down—sometimes, they slip in through the cracks. This month, we’re spotlighting three subtle but serious security risks that could be undermining your defences right now.

This blog post covers the areas shown in our BIM 360 Surgery 'Live Broadcast'
Submit selected project documents or whole folders for review and approval using pre-defined approval workflows.
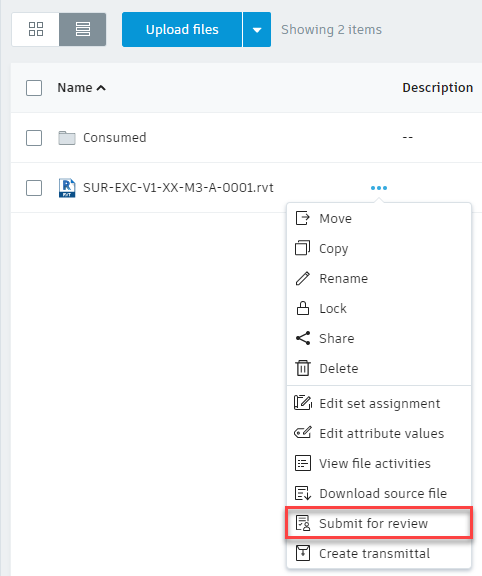
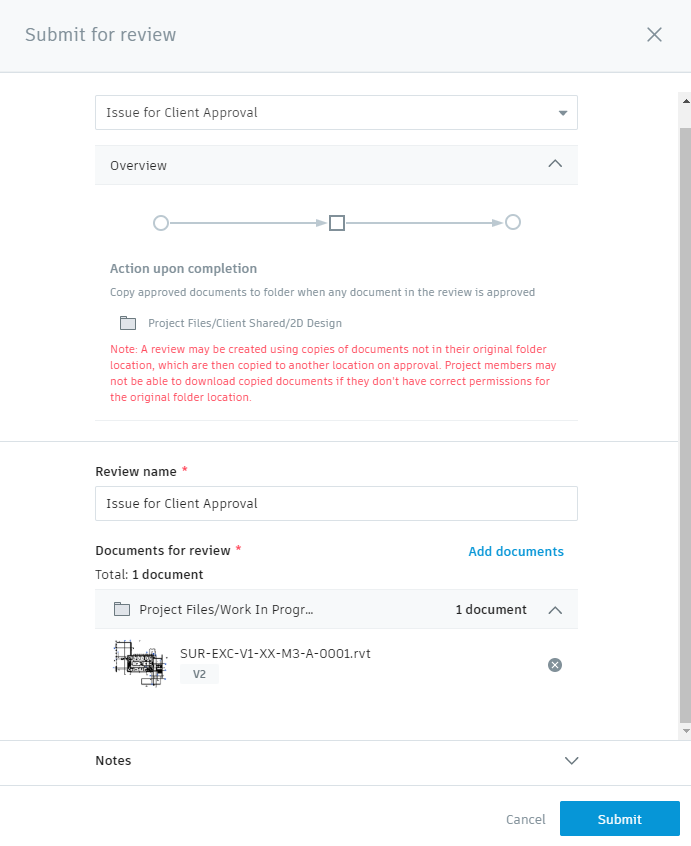
The review is displayed in the Document Management ![]() Reviews tab, awaiting action by the reviewer or approver.
Reviews tab, awaiting action by the reviewer or approver.
You can create a transmittal from an entire folder or from a selection of documents. Note: You must have View + Upload or higher permissions to create transmittals.
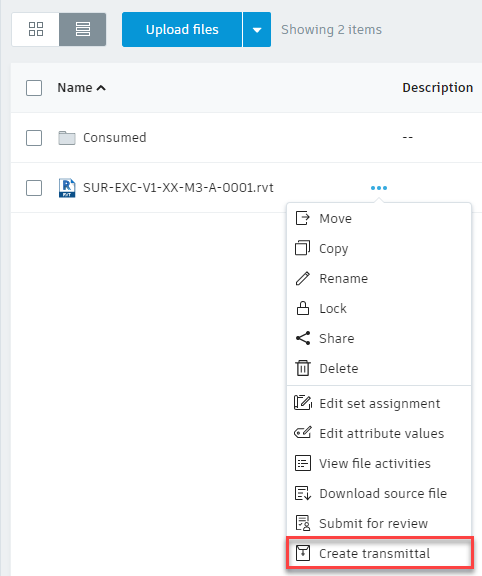
If you select the entire folder, you'll be able to deselect individual documents in the next step. This can be a time saver if you need to share most of the documents in the folder.
Note: Only recipients with access to the selected documents can be added.
If necessary, add a message to the transmittal recipients. The message can indicate what the transmittal is for and specify any required actions.
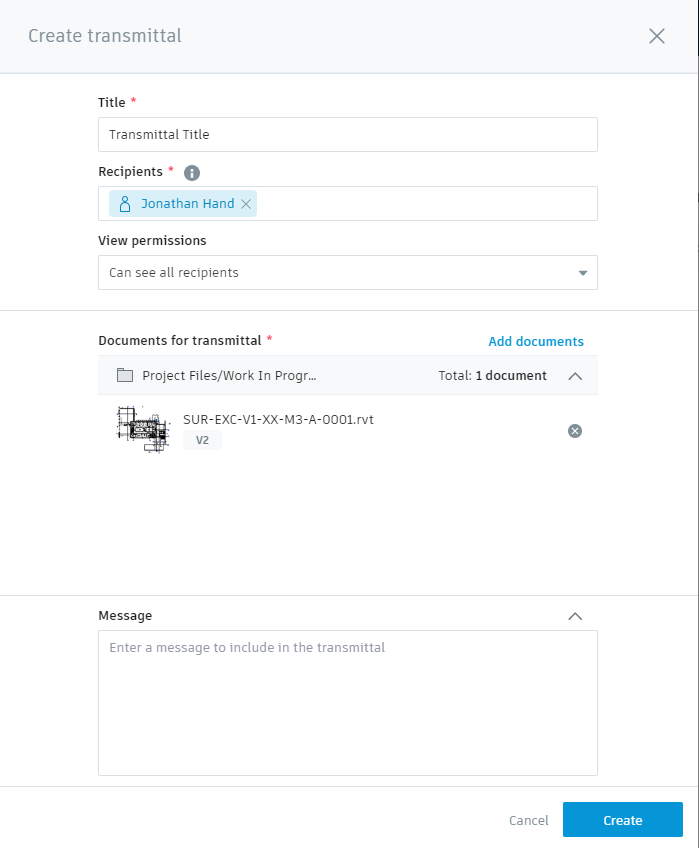
Recipients of the transmittal are notified via email when the transmittal is ready to view.
I hope you found this blog article helpful. See this in action by watching our video: BIM 360 Surgery #34 - Reviews and Transimittals
You can find more information and the latest updates to each module in the BIM 360 portofilio on our YouTube Channel: BIM 360 Surgery Playlist
Note: the above webinar recordings were created by Excitech prior to becoming Symetri in January 2021, following its acquisition by Addnode Group. All Excitech products, services and solutions mentioned in this recording are available through Symetri.
If you would like further information, get in touch with us on 0345 370 1444 or email us at info@symetri.co.uk.
Cybersecurity threats don’t always kick the door down—sometimes, they slip in through the cracks. This month, we’re spotlighting three subtle but serious security risks that could be undermining your defences right now.
As 2025 comes to a close, we’re looking back at some of the most impactful cyber threats of the year and more importantly, what they reveal about the challenges ahead. From ransomware tactics to AI-driven phishing and risky app integrations, this round-up highlights where businesses have been most vulnerable and how you can strengthen your defences in 2026.
Learn what Product Lifecycle Management (PLM) is and how it helps teams manage product data, processes, and collaboration across the lifecycle. Discover the key benefits and PLM tools driving innovation.
