Streamlining Autodesk Deployments: How CQi Simplifies the Installation Process
For many organisations, Autodesk software is mission-critical — used daily across design, engineering, and construction teams.


Any firm of any size has the right to control its own affairs. Sometimes it’s the shareholders that do it but that amounts to the same thing because they own or part-own the firm. Whatever the complexities or simplicities of ownership might be, firms have to be able to run their business the way they want to.
In the construction sector the multitude of designers, contractors and specialist consultants working on a project puts collaboration at the heart of successful project outcomes. Each subcontractor then has two agendas to follow alongside each other; its own, and that of the shared project responsibilities, tasks and deliverables.
Collaboration is about sharing goals and working in a closely-knit fashion to drive a common agenda. It’s about common interests. In a digital world, this puts data in the spotlight; sharing information to make sure everybody’s moving in the agreed direction, nobody is out of kilter, no actions are being taken anywhere in the mix, by any individual organisation, that can adversely impact actions taken by others.
The best place for all this sharing to take place is in an environment that provides common access for all parties to all data – a single version of the truth, a single source of information, aka the Common Data Environment (CDE). The logic of such a repository is sound. The practices it promotes are based on visibility, transparency, and overall project control.
Buried within the entire philosophy and strategy of the CDE is that tiny consideration around controlling your own destiny, regardless of any commitment you make to fulfil your responsibilities with the highest professional standards. ‘All for one and one for all’ can’t be faulted as a guiding principle. It also brings the possibility that you might end up losing your own firm’s tight control of its data when you make it generally available to others.
In my view there are a few areas of potential exposure where it’s important to safeguard against the possibility of losing track of the data you contribute to the CDE. ‘Losing track’ could create headaches further down the line. It’s not beyond the realms of possibility to imagine a situation where disputes arise about who contributed what and when; if versions were not updated when they should have been; if files have been erroneously labelled. Any firm needs its own audit trail that it has complete confidence in.
PAS 1192 shows four states in the CDE: Work-in-Progress, share, publish, and archive. As a reminder, here’s the diagrammatic published by the BSI in relation to the CDE (which they refer to as the Collaborative Data Environment):
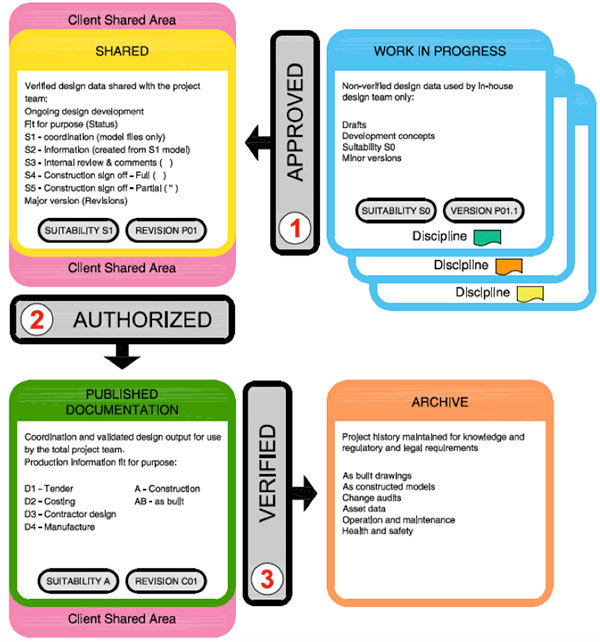
Whilst you have complete control of the first and fourth stages (WIP and archive) the middle stages of ‘share’ and ‘publish’ sit outside your firm’s firewall, in the extranet, and that to me says: ‘Take care’. It’s why you need document management tools (covering structured and unstructured data; anything from emails to transmittal documents) that sit within your firewalls: share all you need to but safeguard your own record of events.
At the same time, serving the interests of the shared project, your own document management tools must be capable of interfacing with the CDE to avoid having to do everything twice. The ideal is to be able simply to hit ‘send’ and the relevant document goes on its way with – due to integral APIs – metadata automatically included; thus eliminating the possibility of human error.
If the project lead has specified certain document conventions, for example to ensure BIM conformity, you need to be able to comply with these requirements, such as MS Office format, .docx rather than .doc and so on. I think the easy answer is to do both; the way the project lead wants the data and the way you want it.
I’ve talked about the audit trail so I’d just like to stress why having your own parallel version of what’s being sent to the CDE is important. This is about speed and reliability. Productivity can be affected if you have to keep uploading to an extranet CDE. Big files can eat up a lot of time. Waiting for them to upload/download can slow down productivity. Also, no matter how digitally savvy we all are nowadays, the problem of dropped connections still comes to haunt us from time to time. Running your own data mirror means you can keep working while files are being synchronised. It’s also about risk. You can’t be certain that the project will go as smoothly as you would wish so you need to be sure that you maintain your own records and copies of files to present as evidence when needed.
There is no such thing as a one-company CDE. When the data is on your territory on your terms, sent on to the project team extranet repositories as required but always originated back home, it can all be created and stored in an efficient Document Management System (DMS). It’s not a revolutionary practice but it is based on logic for the individual firm as sound as the logic that supports the CDE. It offers visibility, transparency, and project control for your participation in the project.
The objection I frequently encounter with customers is that they simply don’t want to use the mandated, or rather specified, CDE. The answer is that if you want the business then you should comply but then make sure you have a robust DMS in place that replicates CDE practices, easily interfaces with the CDE and, above all, keeps you in control of data that’s rightfully yours.
For many organisations, Autodesk software is mission-critical — used daily across design, engineering, and construction teams.
Discover how combining CQFlexMon with CQI provides a complete solution for CAD software deployment and monitoring. Improve software efficiency, reduce risk, and streamline your IT operations.
Cybercriminals are always evolving, and so should your defences. This month, we shine a spotlight on three often-overlooked yet critical security concerns that could put your business at risk.
